Container Security: Exploring Falco’s Features and Threat Detection Capabilities
Introduction
Hello, I’m Emre. I work as a Cloud Native Engineer at Bestcloudfor.me and I’m part of a team that provides consulting services primarily in the AWS cloud domain to our clients.
In this article, I would like to talk to you about Falco, an effective tool for container security. With the rapid proliferation of containerized applications, security concerns have also been on the rise. This is where the importance of a runtime security tool like Falco comes into play.
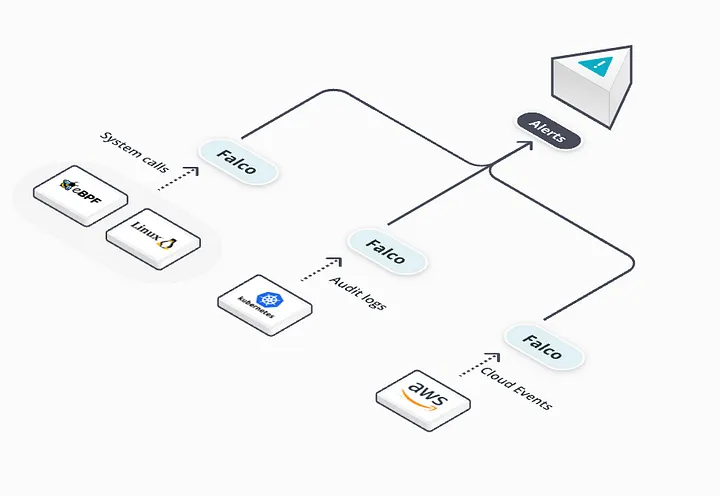
Kubernetes security is a challenging topic due to the dynamic relationships between different application layers and components. To overcome this difficulty, a runtime security tool called Falco has been developed by Sysdig.
Falco is an open-source tool designed to provide security for applications running in your Kubernetes cluster. It uses a set of rules to monitor activities and behaviors to detect potential security breaches.
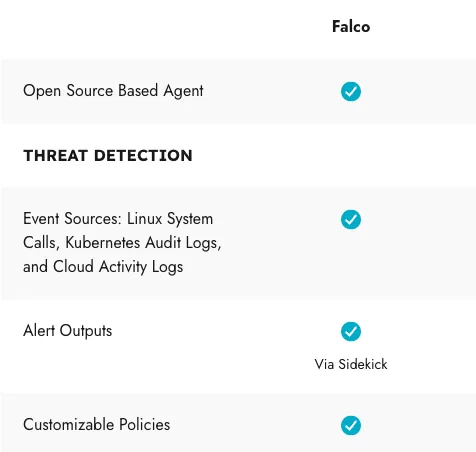
The key features of Falco include working as a runtime security tool that monitors activities of applications running in your Kubernetes cluster. It comes with customizable rules in YAML format. When any attack or misconfigured application is detected, it records events and sends notifications.
Alert mechanism of Falco
Falco comes with a set of predefined alarm rules that monitor the activities of applications running in your Kubernetes cluster and send alerts in case of abnormal behavior. Some examples of these alarm rules are:
Sensitive file access: Sends an alert when access to sensitive files is detected. Shell in Kubernetes Pod: Sends an alert when a shell is detected running within Kubernetes pods. These alarm rules can be easily customized or expanded by editing Falco’s YAML-based rules. When Falco detects unusual activities, it logs these activities and sends notifications to users. Notifications can be sent to Slack, email, Syslog, or any other specified destination. Check https://falco.org/blog/extend-falco-outputs-with-falcosidekick/ website to explore more supported destinations.
Please note that Falco provides the flexibility to tailor the rules according to specific security requirements, allowing you to adapt the monitoring system to your needs and enhance your overall security posture.
You can learn more by visiting Falco’s docs.
Installing and Receiving Alarms with Falco
Falco provides different installation methods and if you refer to the installation documentation, you can find detailed information about each option. Falco does recommend the direct installation on the host system as the preferred method.
The most secure way to run Falco is to install Falco directly on the host system so that Falco is isolated from Kubernetes in the case of compromise. Then the Falco alerts can be consumed through read-only agents running in Kubernetes.
We will proceed with the installation of Falco as a DaemonSet on a Kubernetes cluster using a third Party method.
To install Falco, you need a running Kubernetes cluster. Additionally, this document utilizes the Helm package manager for the installation steps. If you wish to receive notifications through Falco, there are various methods available. However, in this document we will use Slack for demonstration purposes.
After setting up the environment and installing the necessary tools, here are the steps you need to take:
kubectl create ns falco
helm repo add falcosecurity https://falcosecurity.github.io/charts
helm repo update
helm install falco -n falco falcosecurity/falco \
--set auditLog.enabled=true \
--set falco.jsonOutput=true \
--set falco.fileOutput.enabled=true \
--set falcosidekick.enabled=true \
--set falcosidekick.config.slack.webhookurl="<YOUR-SLACK-WEBHOOK-ENDPOINT>"
To verify the installation of Falco, run the following command:
kubectl get pods -n falco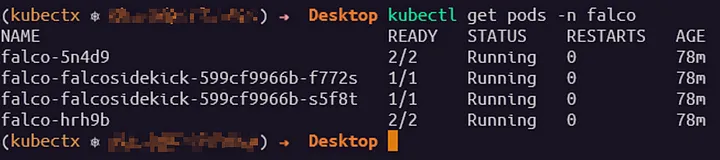
If you see this output, the installation is complete. After that we can do some risky operations and complete the tests.
Example of creating files in /etc directory
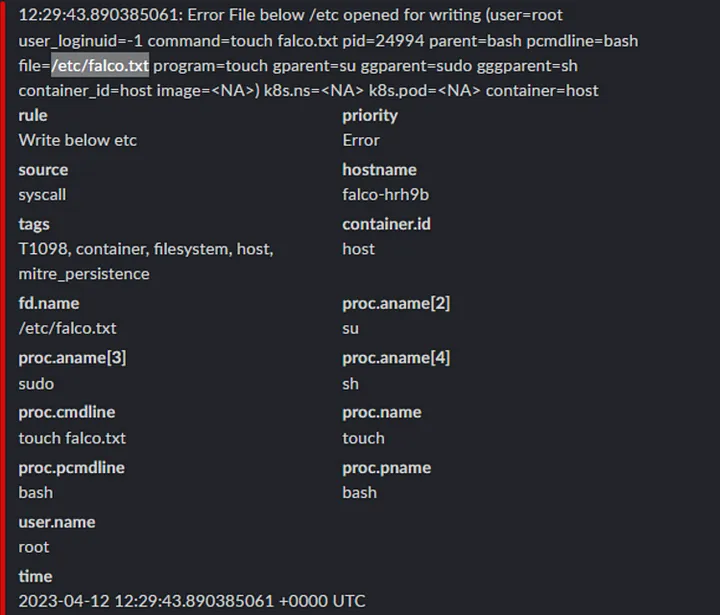
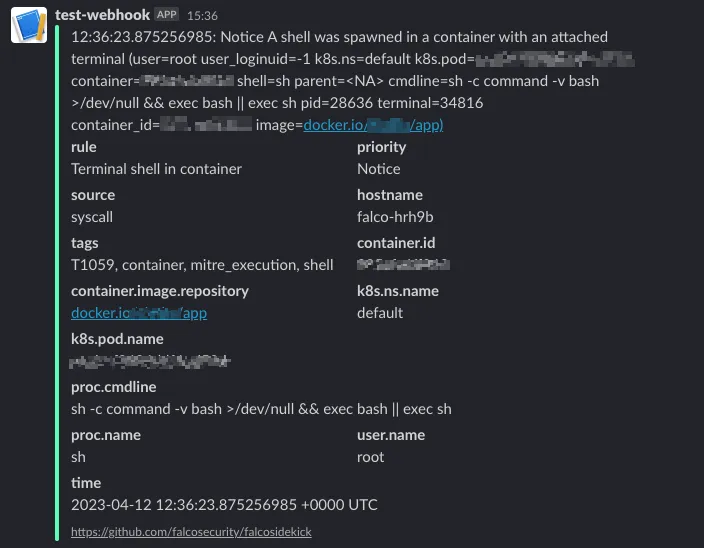
Example of open shell in running pod
Alternatives
There are some alternatives to Falco for monitoring runtime malicious activities for Container Security:
- Sysdig Secure: Sysdig Secure provides a range of tools for monitoring security in container environments and detecting threats. Sysdig has a runtime security engine similar to Falco, providing the ability to detect anomalies and threats in the system.
- Twistlock (Palo Alto Networks — Prisma Cloud): Twistlock is a popular tool that provides a comprehensive platform for container security. It offers runtime detection of malicious activities, identification of weak configurations, and prevention of breaches. These tools are some commonly used alternatives for monitoring and detecting malicious activities in container environments. To determine which tool is best suited for your needs, it’s important to consider your requirements, budget, and priorities.
Conclusion
To sum up, Falco is an essential tool for securing Kubernetes clusters. It provides us with confidence in the security of our applications within the cluster and alerts us to any abnormal activities.
Falco acts as a detection tool and sends alerts regarding the detected events, but it does not actively prevent or block activities. Therefore Falco can be used in conjunction with other tools to take action in response to the identified security issues.
Preventing such malicious activities will be the subject of another article :)